Here’s the simple fix to avoid PrintNightmare exploit on your Windows PC. Act Now!
Your Windows PC – whichever version you are running with, be it Windows 11, Windows 10 or anything before – is at risk of getting PrintNightmare exploit. In case you have not heard anything before about PrintNightmare exploit, read below for the explanation.
- This article detailed the steps to check if your Windows PC is vulnerable to PrintNightmare exploit and show you how to patch fix it.
- In case you have queries, post them on the comment section below.
- For other interesting articles, head to: Windows, Android, iOS, Games and Gaming, Tech, FREE Games and Stuffs and more on JILAXZONE.
- If you find this article / content inside is already obsolete, do let me know by commenting on the comment section below so that I can update the article to reflect the latest process/news. Thanks.
What is PrintNightmare exploit?
PrintNightmare exploit is a vulnerability found on all version of Windows that if exploited, the attacker could run any codes with SYSTEM privileges or in a more friendly statement: attacker can remotely take over your Windows PC. At the time this article is written, Microsoft has assigned this vulnerability with CVE-2021-34527 but has not provided any details yet.
What’s the risk of you don’t take action to patch fix PrintNightmare exploit?
As stated above, if exploited, your Windows PC is at risk of getting remotely controlled and took over by the attacker and with SYSTEM privileges, the attacker could run any codes on your Windows PC. You may end up losing your documents and important files, you may have corrupted Windows PC or in worst case scenario, lose the entire storage.
Here’s what you can do to patch fix PrintNightmare exploit
At the time this article is written, Microsoft is still investigating the issue, but has come out with workarounds to avoid getting exploited by PrintNightmare. So here’s how to patch fix your Windows from PrintNightmare exploit. The steps are pretty easy to be done and will require 5-10 minutes of your time.
1) Ensure you have applied the 8th June 2021 Windows security update.
Follow these steps to check and ensure your have applied the 8th June 2021 Windows Security update.
a) Click Windows icon > Settings > Update & Security > Windows Security.
b) Under Windows Security, click on “Virus & threat protection”.
c) Under Virus & threat protection, check the dates under “Virus & threat protection updates”. If it’s after 8th June 2021, then you are good. But I do recommend you to click on “Check for updates”, just in case there’s newer updates coming from Microsoft.
d) You can close “Windows Security” window for now.
2) Check if your Print Spooler is running
Follow these steps to check if your Print Spooler is running.
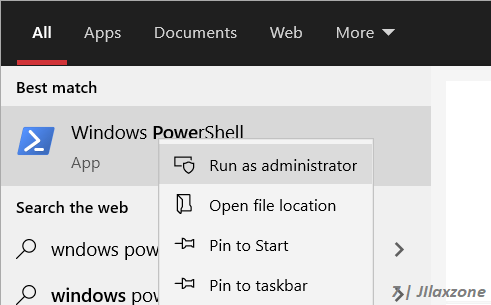
a) Click Windows icon, type “Windows PowerShell”. Click on “Windows PowerShell” to run it.
b) Once Windows PowerShell is opened, type the following command but without the double quotes: “Get-Service -Name Spooler”.
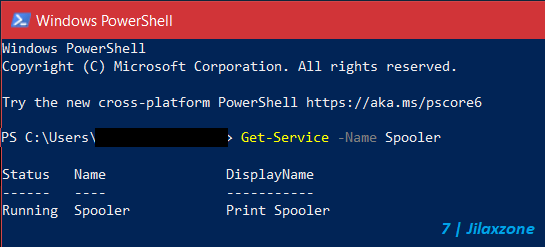
c) Check the status. If the status shown as “Running”, then you need to proceed to the next steps. However if the status shown as “Disabled” or “Stopped”, then you are good to go.
d) Close the Windows PowerShell.
3a) Disable Print Spooler service
Follow these steps to disable Print Spooler service if this is your personal Windows PC or if your Company allows you to have access to PowerShell and enabling/disabling services. Otherwise, proceed to the next step.
a) Reopen Windows PowerShell but this time, to run as Administrator. Click on Windows icon, type “Windows PowerShell”. Do right click on “Windows PowerShell” > “Run as Administrator“. Do key in your Administrator credential when prompted.
b) Windows will then prompt “Do you want this app to make changes to your device?” Click “Yes” to run Windows PowerShell as Administrator.
c) On Windows PowerShell window, type the following command but without the double quotes: “Stop-Service -Name Spooler -Force”. If you are getting error, that means you are not running Windows PowerShell as Administrator.
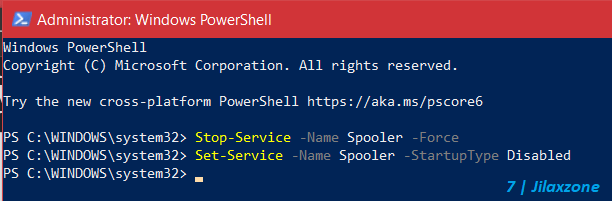
d) Still on Windows PowerShell window, now type the following command but without the double quotes: “Set-Service -Name Spooler -StartupType Disabled”. If you are getting error, that means you are not running Windows PowerShell as Administrator.
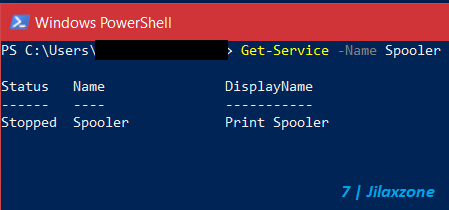
e) Still on Windows PowerShell window, now typethe following command but without the double quotes: “Get-Service -Name Spooler”. If you execute the above codes correctly, you should now see the Print Spooler service has been stopped / disabled.
f) Close the Windows PowerShell.
3b) Disable inbound remote printing through Group Policy
Follow these steps to disable inbound remote printing via Group Policy. By doing this, it will block inbound remote printing operations. Your Windows PC will no longer function as a print server, however the Windows PC can still print out if the printer is directly attached to the PC.
a) Click on Windows icon, type “Edit Group Policy”. Click on “Edit Group Policy” to run it. Do key in your Administrator credential when prompted.
b) Under Group Policy window, navigate to Computer Configuration > Administrative Templates > Printers.
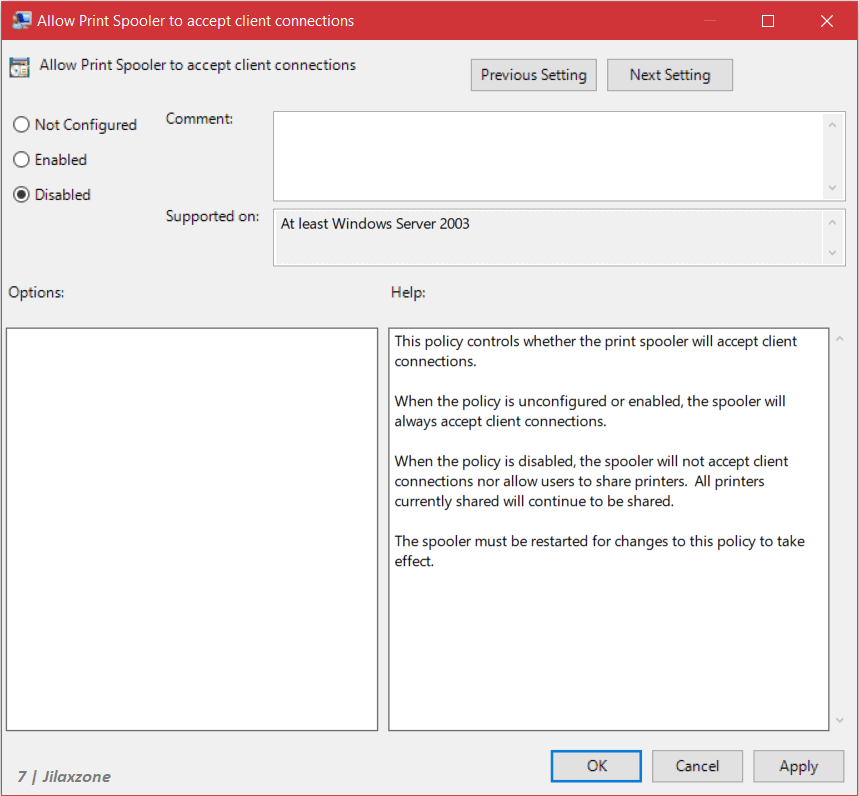
c) Find “Allow Print Spooler to accept client connections” and double click on it to open the setting. Choose “Disabled” and click “OK”.
Act Now. Don’t wait
Be it the Windows computer is yours or your company, act now and don’t wait. The exploit is real and can happen to anyone of us who neglected to take actions to disable the necessary services mentioned above. If the Windows PC belongs to your company and there’s isn’t much you can do to change the settings / policy, contact your Company device’s administrator.
This guide is expanded and detailed from Microsoft official guide for PrintNightmare exploit fix which can be found here: https://msrc.microsoft.com/update-guide/vulnerability/CVE-2021-34527.
Do you have anything you want me to cover on my next article? Write them down on the comment section down below.
Alternatively, find more interesting topics on JILAXZONE:
JILAXZONE – Jon’s Interesting Life & Amazing eXperience ZONE.
Hi, thanks for reading my curated article. Since you are here and if you find this article is good and helping you in anyway, help me to spread the words by sharing this article to your family, friends, acquaintances so the benefits do not just stop at you, they will also get the same goodness and benefit from it.
Or if you wish, you can also buy me a coffee:

Thank you!
Live to Share. Share to Live. This blog is my life-long term project, for me to share my experiences and knowledge to the world which hopefully can be fruitful to those who read them and in the end hoping to become my life-long (passive) income.
My apologies. If you see ads appearing on this site and getting annoyed or disturb by them. As much as I want to share everything for free, unfortunately the domain and hosting used to host all these articles are not free. That’s the reason I need the ads running to offset the cost. While I won’t force you to see the ads, but it will be great and helpful if you are willing to turn off the ad-blocker while seeing this site.